Forescout’s Network Access Control (NAC)
Available on backorder
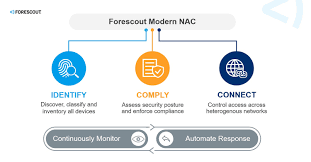
The Forescout Platform is an agentless NAC solution that provides real-time visibility, Zero Trust access control, and automated threat response for all network-connected devices, seamlessly integrating with multi-vendor environments to enhance security and compliance.
Compare
The Forescout Platform is a next-generation, agentless Network Access Control (NAC) solution that delivers comprehensive visibility, automated control, and Zero Trust enforcement for all connected devices across IT, IoT, OT, and IoMT environments. It continuously discovers, classifies, and assesses the security posture of managed and unmanaged devices, including workstations, laptops, IoT devices, medical equipment, and industrial control systems. Forescout enforces least-privilege access policies, automates compliance workflows, and orchestrates threat responses without requiring 802.1X or agents. With over 70 integrations (e.g., Microsoft Azure, ServiceNow, CrowdStrike), it enhances existing security ecosystems by sharing contextual data and automating workflows. The platform supports heterogeneous, multi-vendor networks, making it ideal for enterprises seeking to reduce attack surfaces, ensure compliance (e.g., PCI-DSS, HIPAA), and implement Zero Trust principles without disrupting operations.
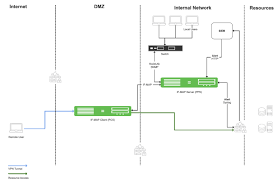
- Architecture:
- Components:
- Forescout Appliance: Handles discovery, classification, assessment, and enforcement; available as physical (CT series) or virtual appliances.
- Forescout Enterprise Manager: Centralizes management for multiple appliances in large deployments.
- Forescout Cloud: Optional cloud-based management for real-time analytics and high-fidelity classification.
- Deployment Options: Physical appliances (CT-1000 to CT-8000), virtual appliances (VMware, Hyper-V, AWS, Azure), cloud-hosted (Azure Marketplace), or hybrid.
- Scalability: Supports millions of devices; appliances can be clustered for high availability and load balancing.
- Operation Mode: Out-of-band (no traffic impact) or inline (real-time traffic control); supports passive-only monitoring for sensitive OT environments.
- Components:
- Discovery and Classification:
- Methods: Over 20 active and passive techniques (e.g., DHCP fingerprinting, SNMP, HTTP/HTTPS, TCP/UDP port scanning, DPI of 250+ protocols, PCAP analysis).
- Capabilities: Identifies device type, OS, manufacturer, and configuration for IT, IoT, OT, and IoMT devices; updates inventory in real time.
- Agentless: No software agents required; optional Secure Connector agent for legacy systems (e.g., Windows XP).
- Authentication:
- Protocols: 802.1X (optional), MAB, Captive Portal, VPN-based authentication.
- Integrations: Active Directory, LDAP, SAML, RADIUS, and third-party IdPs (e.g., Okta).
- Pre-Connect/Post-Connect: Enforces policies before or after network access, balancing security and user experience.
- Policy Enforcement:
- Mechanisms: VLAN steering, ACLs, port control, network segmentation, quarantine, and least-privilege access.
- Policies: Granular, based on user identity, device type, compliance status, and risk posture.
- Zero Trust: Ensures only authenticated, compliant devices access resources.
- Compliance Assessment:
- Checks: Security hygiene (e.g., antivirus, patches, firewall status), compliance with standards (e.g., PCI-DSS, HIPAA, GDPR).
- Automation: Triggers remediation workflows (e.g., patch installation, agent repair) or restricts access for non-compliant devices.
- Threat Containment:
- Actions: Quarantine, block, VLAN reassignment, port shutdown, or ticket generation.
- Automation: Responds to anomalies, rogue devices, or non-compliance in real time.
- Integrations: Shares threat context with SIEM, XDR, and firewalls for coordinated response.
- Segmentation:
- eyeSegment Module: Automates dynamic network segmentation without infrastructure changes.
- Controls: Enforces micro-segmentation to limit lateral movement, reducing blast radius.
- Integrations:
- Ecosystem: Over 70 third-party tools (e.g., Microsoft Azure, ServiceNow, CrowdStrike, Palo Alto Networks, Splunk, SCCM).
- eyeExtend: Enables bidirectional data sharing and workflow orchestration via APIs and plug-and-play modules.
- Network Devices: Vendor-agnostic, supports Cisco, Juniper, Aruba, and over 150 switch/AP vendors.
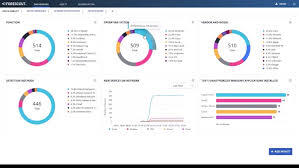
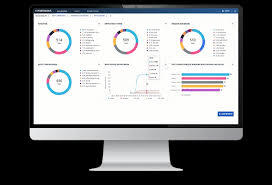
- Visibility:
- Real-time dashboards and persona-based reports (executive, SOC, IT operations).
- Tracks device inventory, compliance status, and network connections for auditing.