Ivanti Neurons for Risk-Based Vulnerability Management
Ivanti Neurons for Risk-Based Vulnerability Management prioritizes critical vulnerabilities, streamlining remediation with real-time analytics and automation. Secure your business now!
Ivanti Neurons for Risk-Based Vulnerability Management: Secure Your Digital Future
Why Choose Ivanti Neurons for Risk-Based Vulnerability Management?
In today’s digital landscape, cyber threats evolve rapidly. Ivanti Neurons for Risk-Based Vulnerability Management (RBVM) empowers organizations to stay ahead. This SaaS solution prioritizes vulnerabilities based on real risk, streamlining remediation efforts. Unlike traditional tools, it focuses on critical weaknesses, ensuring efficient protection against data breaches. By leveraging advanced analytics, Ivanti Neurons transforms your cybersecurity strategy, delivering proactive defense. This platform suits businesses of all sizes, offering unmatched scalability and ease of use.
Key Features of Ivanti Neurons RBVM
Ivanti Neurons RBVM stands out with cutting-edge features. First, it uses risk-based prioritization to identify high-impact vulnerabilities. Next, its SaaS delivery ensures seamless updates and accessibility. Additionally, the platform integrates with existing IT systems, enhancing workflow efficiency. Real-time analytics provide actionable insights, while automated processes reduce manual workloads. Furthermore, its user-friendly interface simplifies complex tasks, making it ideal for IT teams. These features collectively strengthen your cybersecurity posture, minimizing breach risks effectively.
Benefits of Risk-Based Vulnerability Management
Implementing Ivanti Neurons RBVM offers numerous advantages. It accelerates vulnerability prioritization, saving valuable time. Moreover, it reduces remediation costs by focusing on critical threats. The platform enhances compliance with industry regulations, avoiding costly penalties. Additionally, it boosts team productivity through automation, freeing resources for strategic tasks. By proactively addressing vulnerabilities, businesses protect sensitive data and maintain customer trust. Consequently, Ivanti Neurons RBVM delivers measurable ROI and long-term security.
How Ivanti Neurons RBVM Works
Ivanti Neurons RBVM operates with precision and simplicity. Initially, it scans your IT environment to detect vulnerabilities. Then, it assesses risks using advanced algorithms, prioritizing threats based on severity. Next, it provides clear remediation steps, guiding IT teams efficiently. The platform continuously monitors systems, ensuring real-time protection. Moreover, it generates detailed reports for compliance and auditing purposes. This streamlined process ensures robust security without overwhelming your team.
Why Ivanti Neurons RBVM Excels in Cybersecurity
Ivanti Neurons RBVM outperforms competitors by focusing on risk-based strategies. Unlike generic tools, it tailors solutions to your unique environment. Its cloud-based architecture ensures flexibility and scalability, adapting to growing needs. Additionally, Ivanti’s commitment to innovation keeps the platform ahead of emerging threats. By integrating with other Ivanti solutions, it creates a cohesive security ecosystem. This holistic approach makes Ivanti Neurons RBVM a leader in vulnerability management.
Who Should Use Ivanti Neurons RBVM?
This solution targets IT professionals, security teams, and business leaders. Small businesses benefit from its affordability and ease of use. Meanwhile, large enterprises leverage its scalability for complex environments. Additionally, industries like healthcare and finance, with strict compliance needs, find it invaluable. By addressing diverse requirements, Ivanti Neurons RBVM ensures broad applicability across sectors.
Get Started with Ivanti Neurons RBVM Today
Ready to enhance your cybersecurity? Ivanti Neurons RBVM offers a powerful, user-friendly solution to protect your organization. Start prioritizing vulnerabilities effectively and safeguard your digital assets now. Explore the platform’s capabilities and transform your security strategy today.
View Ivanti Resource Document (ID: 2673)
Visit Cybersecurity Products at Kysinfotech
-
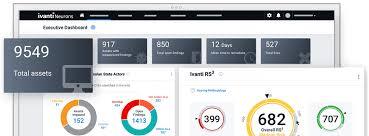
Technical Specifications
Feature Description Data Sources Internal scanners, pen tests, 100+ external feeds Risk Prioritization Proprietary VRR, Ivanti RS3, asset criticality scoring Threat Intelligence AI- and analyst-curated, ransomware-focused Automation Playbooks, SLA enforcement, custom alerts Dashboards Role-based, customizable with widgets and filters Compliance Filters CISA Top 10, CVEs, XSS, WannaCry, BlueKeep Integration Compatible with Ivanti Neurons for ITSM Collaboration Tools Deep links, dashboard sharing, export templates Deployment Cloud-based SaaS solution
Related products
-
Software
Ivanti Neurons for HR
Ivanti Neurons for HR modernizes HR service delivery with automated workflows, AI-powered case management, and self-service portals. Designed for today’s digital workforce, it empowers HR teams to streamline processes, enhance employee experiences, and reduce operational costs.
SKU: ivanti-neurons-hr -
NAC, Network Security, Software
Ivanti Policy Secure (IPS)
Ivanti Policy Secure (IPS) is a network access control solution that ensures zero trust security for all endpoints, including IoT and BYOD. It provides visibility, granular policy enforcement, and automated threat response for the Everywhere Workplace.
SKU: ivanti-policy-secure -
Endpoint Management, MDM, Software
ManageEngine Mobile Device Manager Plus
ManageEngine Mobile Device Manager Plus delivers secure mobile device management for enterprises. Supports iOS, Android, Windows, and macOS with app control, geofencing, and remote troubleshooting.
SKU: manageengine-mobile-device-manager-plus