Why Choose Cisco Identity Services Engine (ISE) for Enterprise Security?
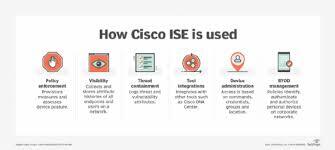
Centralized Access Control and Visibility
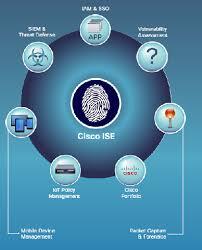
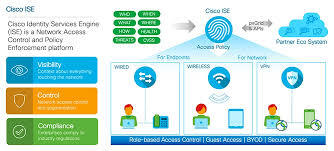
Cisco ISE is a powerful network access control (NAC) platform. It unifies authentication, authorization, and accounting for all users and devices. It enables businesses to enforce consistent access policies across wired, wireless, and VPN connections.
With ISE, IT teams gain real-time visibility into every connected endpoint. This improves security posture and reduces operational risks.
- Controls network access from a single dashboard.
- Identifies and classifies endpoints in real time.
- Works across multi-vendor networking environments.
Advanced Threat Defense Integration
Cisco ISE integrates seamlessly with threat detection tools like Cisco SecureX, Firepower, and Stealthwatch. These integrations enable automated threat response. When suspicious activity is detected, ISE can instantly quarantine or block the affected device.
- Automates incident response for faster remediation.
- Connects to third-party SIEM and threat platforms.
- Improves compliance with regulatory frameworks.
Policy-Based Network Segmentation
ISE allows granular segmentation using software-defined access (SD-Access). This isolates sensitive resources from general traffic. The result is reduced lateral movement for attackers and improved containment of security breaches.
- Creates dynamic network segments for user groups.
- Applies different access rights based on device posture.
- Integrates with Cisco DNA Center for automation.
Secure BYOD and Guest Access
Bring-Your-Own-Device policies are easier to manage with Cisco ISE. Employees and guests can self-register devices through a secure portal. ISE ensures each device meets compliance standards before granting access.
- Streamlined guest onboarding without IT intervention.
- Compliance checks before network entry.
- Customizable access portals for branding.
Scalable for Modern Enterprises
From small businesses to global corporations, Cisco ISE scales easily. Its architecture supports high availability, redundancy, and cloud or on-premises deployment.
- Flexible licensing options to match business needs.
- High-performance processing for large user bases.
- Supports hybrid and multi-cloud environments.
Conclusion: Cisco ISE Delivers Trusted, Adaptive Security
Cisco Identity Services Engine is more than an access control tool. It is a unified security policy engine that adapts to evolving threats. For enterprises seeking strong compliance, seamless integration, and automated responses, ISE is a strategic investment.
Visit KYS Infotech Cisco Brand Page
Download Cisco Identity Services Engine (ISE) Data Sheet (PDF)
Technical Specifications for Cisco Identity Services Engine (ISE)
-
Platform: Physical or virtual appliance (VMware ESXi 6.5+, KVM, Hyper-V)
-
Versions: ISE 3.x (latest: 3.4)
-
Authentication: 802.1X, EAP, RADIUS, TACACS+
-
Policy Enforcement: TrustSec, Software-Defined Segmentation
-
Visibility: Device profiling, posture assessment
-
Management: Centralized GUI, Cisco DNA Center integration
-
Deployment: On-premises, multi-cloud, IaC
-
Compliance: GDPR, HIPAA
-
Protocols: pxGrid, ONVIF
-
Security Features: BYOD, guest access, threat containment
-
Operating Temperature: -5°C to 45°C
-
Scalability: Supports clusters for redundancy