Forescout Platform NAC
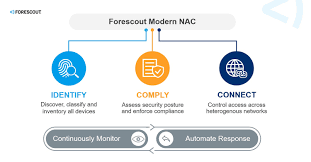
The Forescout Platform NAC revolutionizes Network Access Control (NAC) with agentless, comprehensive visibility and automated Zero Trust enforcement. It dynamically discovers, classifies, and evaluates all connected devices—IT, IoT, OT, and IoMT—ensuring robust security across diverse environments. By enforcing least-privilege access and automating compliance, Forescout minimizes risks without disrupting operations. With seamless integrations like Microsoft Azure and CrowdStrike, it enhances your security ecosystem. Ideal for enterprises, this platform reduces attack surfaces and ensures compliance with standards like PCI-DSS and HIPAA.
Available on Request
Revolutionize Network Security with Forescout Platform NAC
You need robust Network Access Control today. Forescout Platform NAC delivers it. It features a powerful, agentless architecture. This setup fits complex digital environments perfectly.
First, understand its core benefits. It offers real-time visibility. You control all connected devices easily. These include IT workstations and BYOD gadgets. Additionally, it handles IoT sensors and OT equipment. It even manages IoMT devices in healthcare.
Importantly, no software agents required. Forget 802.1X protocols too. Organizations deploy it rapidly. They scale operations without hassle. Existing network infrastructure stays unchanged.
This approach saves time. It cuts costs significantly. Moreover, it boosts security posture overall.
Discover Devices Continuously for Better Visibility
Forescout NAC discovers devices non-stop. It profiles them accurately. The system classifies endpoints across segments.
Next, it evaluates security posture dynamically. You spot risks in real time. For example, identify unauthorized devices quickly.
Additionally, automate policy enforcement. Base rules on risk levels. Consider behavior and roles too. Only authorized devices connect.
Compliant ones stay online safely. This method slashes cyber threats. It thrives in multi-vendor setups.
Furthermore, handle heterogeneous environments effortlessly. Transition smoothly between tasks.
Enhance Compliance with Automated Tools
Compliance matters in every industry. Forescout aligns with key standards. These include PCI-DSS and HIPAA.
It supports NERC CIP and GDPR too. Automate enforcement actions directly. Reduce manual efforts drastically.
For instance, audit trails generate automatically. Reports comply with regulations seamlessly.
Moreover, integrate with top solutions. Connect to over 70 cybersecurity tools. Partners include Microsoft Azure and ServiceNow.
Add CrowdStrike for threat detection. Use Splunk for analytics. Include Palo Alto Networks for firewalls.
This ecosystem automates responses. Share intelligence across platforms. Streamline operations effectively.
As a result, teams respond faster. They mitigate incidents promptly. Efficiency rises across the board.
Adapt Flexibly to Diverse Environments
Secure critical infrastructure now. Forescout adapts to smart buildings. It protects clinical networks too.
Support Zero Trust initiatives easily. Implement segmentation strategies without complexity.
Its agentless design shines here. Manage unmanaged systems well. Handle legacy equipment in OT settings.
In healthcare, control IoMT devices securely. Avoid disruptions to patient care.
Additionally, passive monitoring ensures safety. No active scans needed. Devices remain operational always.
For example, in manufacturing, monitor OT gear. Prevent downtime from security checks.
This flexibility sets Forescout apart. It suits varied use cases perfectly.
Gain Complete Device Intelligence and Control
Enterprises transform security with Forescout. They enforce policies efficiently. Visibility improves at scale.
Maintain compliance without compromise. Access control becomes seamless.
Why choose this platform? It reduces exposure to threats. Organizations trust it worldwide.
In fact, it handles diverse devices. From laptops to sensors, all covered.
Moreover, no agents mean less overhead. Deployment happens in days, not months.
Scalability supports growth. Add devices without worry.
Ultimately, Forescout empowers teams. They focus on strategy, not firefighting.
This NAC solution leads the market. It redefines access control standards.
Explore its features today. See the difference yourself.
- Architecture:
- Components:
- Forescout Appliance: Handles discovery, classification, assessment, and enforcement; available as physical (CT series) or virtual appliances.
- Forescout Enterprise Manager: Centralizes management for multiple appliances in large deployments.
- Forescout Cloud: Optional cloud-based management for real-time analytics and high-fidelity classification.
- Deployment Options: Physical appliances (CT-1000 to CT-8000), virtual appliances (VMware, Hyper-V, AWS, Azure), cloud-hosted (Azure Marketplace), or hybrid.
- Scalability: Supports millions of devices; appliances can be clustered for high availability and load balancing.
- Operation Mode: Out-of-band (no traffic impact) or inline (real-time traffic control); supports passive-only monitoring for sensitive OT environments.
- Components:
- Discovery and Classification:
- Methods: Over 20 active and passive techniques (e.g., DHCP fingerprinting, SNMP, HTTP/HTTPS, TCP/UDP port scanning, DPI of 250+ protocols, PCAP analysis).
- Capabilities: Identifies device type, OS, manufacturer, and configuration for IT, IoT, OT, and IoMT devices; updates inventory in real time.
- Agentless: No software agents required; optional Secure Connector agent for legacy systems (e.g., Windows XP).
- Authentication:
- Protocols: 802.1X (optional), MAB, Captive Portal, VPN-based authentication.
- Integrations: Active Directory, LDAP, SAML, RADIUS, and third-party IdPs (e.g., Okta).
- Pre-Connect/Post-Connect: Enforces policies before or after network access, balancing security and user experience.
- Policy Enforcement:
- Mechanisms: VLAN steering, ACLs, port control, network segmentation, quarantine, and least-privilege access.
- Policies: Granular, based on user identity, device type, compliance status, and risk posture.
- Zero Trust: Ensures only authenticated, compliant devices access resources.
- Compliance Assessment:
- Checks: Security hygiene (e.g., antivirus, patches, firewall status), compliance with standards (e.g., PCI-DSS, HIPAA, GDPR).
- Automation: Triggers remediation workflows (e.g., patch installation, agent repair) or restricts access for non-compliant devices.
- Threat Containment:
- Actions: Quarantine, block, VLAN reassignment, port shutdown, or ticket generation.
- Automation: Responds to anomalies, rogue devices, or non-compliance in real time.
- Integrations: Shares threat context with SIEM, XDR, and firewalls for coordinated response.
- Segmentation:
- eyeSegment Module: Automates dynamic network segmentation without infrastructure changes.
- Controls: Enforces micro-segmentation to limit lateral movement, reducing blast radius.
- Integrations:
- Ecosystem: Over 70 third-party tools (e.g., Microsoft Azure, ServiceNow, CrowdStrike, Palo Alto Networks, Splunk, SCCM).
- eyeExtend: Enables bidirectional data sharing and workflow orchestration via APIs and plug-and-play modules.
- Network Devices: Vendor-agnostic, supports Cisco, Juniper, Aruba, and over 150 switch/AP vendors.
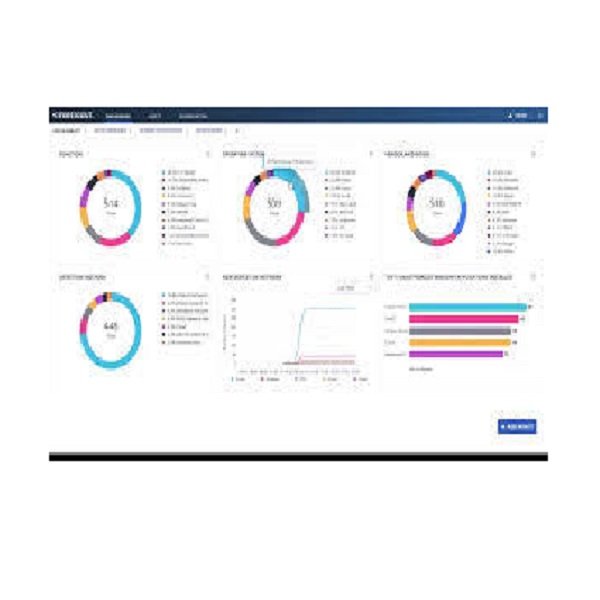
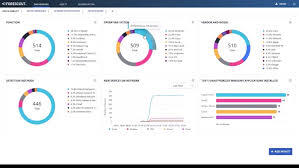
- Visibility:
- Real-time dashboards and persona-based reports (executive, SOC, IT operations).
- Tracks device inventory, compliance status, and network connections for auditing.