Fortinet’s Network Access Control (NAC)
Available on backorder
FortiNAC is a zero-trust NAC solution that provides real-time visibility, dynamic access control, and automated threat response for all network-connected devices, integrating seamlessly with the Fortinet Security Fabric and multi-vendor infrastructure.
Compare
FortiNAC is Fortinet’s zero-trust Network Access Control (NAC) solution that enhances the Fortinet Security Fabric by delivering comprehensive visibility, granular control, and automated response for all devices and users connecting to wired and wireless networks. Designed to secure IT, IoT, OT/ICS, and IoMT environments, FortiNAC discovers and profiles devices in real time, enforces dynamic access policies, and orchestrates rapid threat containment. It supports multi-vendor environments, integrating with over 150 vendors’ network devices (switches, wireless access points, firewalls) to leverage existing infrastructure. Key features include agentless scanning, micro-segmentation, automated onboarding for BYOD and guests, and integration with FortiGate firewalls and other Security Fabric components for enhanced threat intelligence and policy enforcement. FortiNAC is ideal for organizations seeking to protect against IoT threats, ensure compliance, and simplify network access management across single or multi-site deployments.
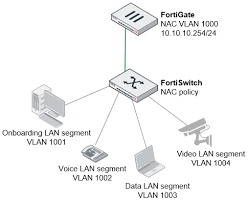
- Architecture:
- Components:
- Control and Application Server: Handles device profiling, policy enforcement, and network orchestration. Can be deployed as a single server for smaller setups or multiple servers for scalability.
- Management Server (FNC-M-550C): Optional for managing multiple appliances in large deployments.
- Deployment Options: Hardware appliances (FNC-CA-500C, FNC-CA-600C, FNC-CA-700C), virtual machines (VMware, Hyper-V, AWS, Azure, KVM), or next-gen VMs for cloud environments.
- Scalability: Unlimited concurrent ports; servers can be stacked for increased capacity, supporting millions of devices across multi-site locations.
- Out-of-Band: Operates outside user traffic, enabling centralized management of remote locations without impacting performance.
- Components:
- Authentication:
- Protocols: 802.1X, MAC Address Bypass (MAB), Captive Portal, VPN-based authentication.
- Methods: Supports agent-based (persistent/dissolvable) and agentless scanning for device detection.
- Integrations: Active Directory, LDAP, RADIUS, SAML, and third-party IdPs for user authentication.
- Profiling:
- Methods: Up to 17 profiling techniques, including DHCP fingerprinting, TCP/UDP port scanning, SNMP, HTTP/HTTPS analysis, and passive traffic analysis via FortiGate integration.
- Capabilities: Identifies device type, OS, manufacturer, and behavior for IT, IoT, and headless devices.
- Policy Enforcement:
- Mechanisms: Dynamic VLAN steering, micro-segmentation, role-based access control, and network lockdown.
- Policies: Granular access based on user identity, device type, security posture, and location.
- Micro-segmentation: Restricts device access to specific network resources, limiting lateral movement.
- Automated Response:
- Triggers: Configurable automation policies for events like non-compliant devices, anomalous behavior, or security alerts.
- Actions: Quarantine, VLAN reassignment, port shutdown, or notifications to administrators.
- Speed: Responds in seconds to contain threats before they spread.
- Visibility:
- Real-time monitoring of all connected devices and users, with detailed dashboards and granular reporting.
- Tracks endpoint behavior, compliance status, and network access events for audit purposes.
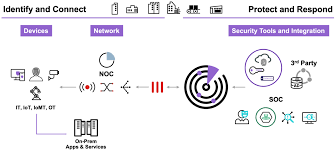
- Integrations:
- Fortinet Security Fabric: FortiGate, FortiAP, FortiSwitch, FortiAnalyzer, FortiSIEM for enhanced visibility and threat response.
- Third-Party: Over 150 vendors (e.g., Cisco, Aruba, Juniper) for switches, APs, and firewalls; integrates with SIEM, MDM, and endpoint protection platforms via APIs.
- Fabric-Ready Partners: Example: Ordr for IoMT device management in healthcare