Portnox Cloud NAC: Zero Trust Network Access Control Solution
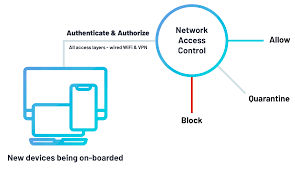
Portnox Cloud NAC delivers a cloud-native, vendor-agnostic Network Access Control (NAC) solution, ensuring Zero Trust security for enterprise networks. This SaaS-based platform simplifies authentication, risk monitoring, and compliance enforcement across wired, wireless, and VPN connections. Supporting managed devices, BYOD, IoT, and OT endpoints, it eliminates on-premises hardware and complex setups. With cloud-native RADIUS, TACACS+, and passwordless authentication, Portnox Cloud offers real-time visibility and automated remediation. Seamlessly integrating with Azure AD, Okta, and SIEMs, it ensures compliance with GDPR, HIPAA, and PCI-DSS, making it ideal for resource-constrained IT teams managing distributed networks.
Available on Request
Portnox Cloud NAC revolutionizes network security with a 100% cloud-native, vendor-agnostic Network Access Control (NAC) solution. Designed for Zero Trust, it secures enterprise networks, applications, and infrastructure by unifying authentication, risk mitigation, and compliance enforcement. Unlike traditional NAC systems, Portnox requires no on-premises hardware or complex configurations, enabling rapid deployment in minutes. It supports wired, wireless, and VPN connections, ensuring secure access for managed devices, BYOD, IoT, and OT endpoints. Additionally, its scalability suits organizations of all sizes, from mid-market to large enterprises.
Moreover, Portnox Cloud NAC offers robust features like cloud-native RADIUS and TACACS+ for seamless authentication and authorization. Its passwordless, certificate-based authentication enhances security while improving user experience. The platform continuously monitors endpoint risk 24/7, automatically remediating non-compliant devices to maintain compliance with standards like GDPR, HIPAA, and PCI-DSS. Furthermore, integrations with identity providers such as Azure AD and Okta, alongside SIEMs and MDM/UEM platforms, provide real-time visibility and granular policy enforcement.
For IT teams managing distributed networks, Portnox Cloud simplifies operations. Its SaaS-based architecture eliminates maintenance headaches, offering affordability and ease of use. By leveraging advanced IoT fingerprinting, it identifies over 260,000 unique devices, ensuring comprehensive network visibility. Consequently, Portnox Cloud empowers organizations to strengthen their security posture, reduce risks, and meet regulatory requirements efficiently.
Portnox Cloud: Simplified, secure NAC.
- Architecture:
- Components:
- Portnox Cloud: Fully SaaS-based platform hosted on Azure, providing RADIUS, TACACS+, policy management, and analytics.
- AgentP: Optional lightweight agent for endpoint risk assessment and remediation (Windows, macOS, Linux, iOS, Android).
- AD Broker: Lightweight software for Active Directory authentication and access controls.
- Analytical Engine: Continuous device risk posture monitoring and policy alignment.
- Deployment Options: 100% cloud-native (Azure-hosted); optional local VMs for RADIUS backup or TACACS+ record keeping. On-premises option available via Portnox CORE.
- Scalability: Scales to millions of devices across distributed networks; supports 10 to 10,000+ devices without hardware upgrades.
- Operation Mode: Out-of-band, integrating with existing network infrastructure (switches, APs, routers) via RADIUS/TACACS+ configurations.
- Components:
- Authentication:
- Protocols: 802.1X (TLS/TTLS, PEAP-MSCHAPv2), MAC Authentication Bypass (MAB), Captive Portal, RadSec, RADIUS Proxy.
- Methods: Passwordless certificate-based authentication (via Portnox Certificate Authority or third-party CA), SSO (SAML 2.0), two-factor authentication for VPN.
- Integrations: Active Directory, Azure AD, Google Workspace, Okta, Open LDAP, SCEP for certificate enrollment.
- Security: All API calls use periodically rotated tokens; no anonymous calls or trusted IP caches. Data encrypted in transit (TLS) and at rest (Azure Cosmos DB).
- Profiling:
- Methods: DHCP fingerprinting, MAC OUI, HTTP/HTTPS analysis, network telemetry; optional AI-powered IoT fingerprinting add-on for enhanced accuracy.
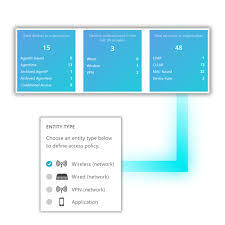
- Capabilities: Identifies device type, OS, location, and access layer (wired, Wi-Fi, VPN); supports managed, BYOD, IoT, and OT devices.
- Agentless: Uses root certificates, SCEP, or MDM (e.g., Intune) for profiling; AgentP for deeper inspection.
- Policy Enforcement:
- Mechanisms: Dynamic VLAN assignment, ACLs, auto-segmentation, role-based access, risk-based access controls, port lockdown.
- Policies: Configurable based on roles, locations, device types, risk scores, and compliance status.
- Risk Engine: Continuously monitors endpoint risk (e.g., antivirus, patches, unauthorized peripherals) and adjusts access dynamically.
- Compliance Assessment:
- Checks: Firewall status, antivirus updates, OS patches, drive encryption, Windows registry keys, passcodes, and application compliance.
- Methods: Agentless (via MDM, certificates) or AgentP for real-time remediation.
- Actions: Quarantine, block, alert, or auto-remediate non-compliant devices.
- Threat Containment:
- Actions: Quarantine vulnerable devices, update firewalls/antivirus, switch to restricted VLAN, or deny access.
- Automation: Triggers responses based on risk scores or SIEM alerts within seconds.
- Integrations: SIEM (e.g., Splunk), firewalls, and XDR for coordinated response.
- Guest Access:
- Features: Role-based policies for guests/contractors, self-service portals, and credential delivery.
- Automation: Simplifies guest management with data loss prevention controls.
- Integrations:
- Identity: Azure AD, Okta, Google Workspace, Active Directory, Open LDAP.
- Security: SIEMs, firewalls, MDM/UEM (e.g., Intune, Jamf), XDR, and endpoint protection platforms.
- Network Devices: Vendor-agnostic, supports Cisco, Aruba, Juniper, Fortinet, and others via RADIUS/TACACS+.
- APIs: REST APIs for custom integrations; syslog for event logging.
- Visibility:
- Dashboards: Real-time visibility of endpoints, locations, device types, and risk postures.
- Reports: Device visibility, connection timelines, guest access history, and compliance adherence.
- Logs: Exportable for audits