Ivanti Neurons for EASM – External Attack Surface Management
Ivanti Neurons for EASM secures your digital assets with AI-driven insights, continuous monitoring, and seamless integration for robust cybersecurity.
Ivanti Neurons for EASM: Comprehensive External Attack Surface Management
Discover Ivanti Neurons for EASM
Ivanti Neurons for External Attack Surface Management (EASM) empowers businesses to secure their digital landscape effectively. This advanced solution proactively identifies, monitors, and mitigates vulnerabilities across your external attack surface. By leveraging cutting-edge technology, it ensures robust protection against cyber threats. Organizations gain real-time visibility into assets, enabling swift action to safeguard sensitive data.
Why Choose Ivanti Neurons for EASM?
Firstly, Ivanti Neurons for EASM offers unparalleled visibility into external assets. It scans websites, cloud services, and third-party integrations comprehensively. Additionally, the platform prioritizes risks based on severity, streamlining remediation efforts. Unlike traditional tools, it integrates seamlessly with existing security frameworks. Consequently, businesses reduce exposure to cyber risks efficiently.
Moreover, the solution employs AI-driven analytics to detect shadow IT and misconfigurations. This proactive approach prevents potential breaches before they occur. Furthermore, its user-friendly interface simplifies complex security tasks. Teams can focus on strategic initiatives rather than manual processes. Thus, Ivanti Neurons for EASM enhances operational efficiency significantly.
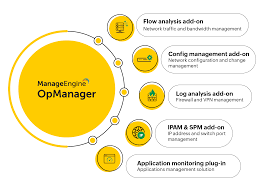
Key Features of Ivanti Neurons for EASM
-
Asset Discovery: Automatically identifies all external assets, including domains and IP addresses.
-
Risk Prioritization: Ranks vulnerabilities by severity for targeted remediation.
-
Continuous Monitoring: Provides real-time updates on emerging threats and changes.
-
AI-Powered Insights: Detects shadow IT and misconfigurations with advanced analytics.
-
Seamless Integration: Works with existing security tools for a unified approach.
-
Compliance Support: Aligns with industry standards to ensure regulatory adherence.
These features collectively strengthen your cybersecurity posture. For instance, continuous monitoring keeps you ahead of evolving threats. Similarly, AI-powered insights enable rapid response to potential risks. As a result, businesses maintain a secure and compliant digital environment.
Benefits for Your Organization
Ivanti Neurons for EASM delivers measurable benefits. It reduces the attack surface by identifying vulnerabilities early. Additionally, it saves time through automated processes, freeing up IT teams. Moreover, the platform enhances decision-making with actionable insights. Organizations can allocate resources effectively, focusing on high-priority risks. Consequently, this leads to improved security and reduced operational costs.
Furthermore, the solution supports compliance with regulations like GDPR and HIPAA. By ensuring adherence, it minimizes legal and financial risks. Ultimately, Ivanti Neurons for EASM fosters trust among stakeholders and customers.
Who Needs Ivanti Neurons for EASM?
This solution suits businesses of all sizes across industries. IT teams, security professionals, and compliance officers benefit significantly. For example, enterprises with complex digital ecosystems rely on its robust capabilities. Similarly, small businesses gain affordable, enterprise-grade protection. Therefore, it’s a versatile tool for modern cybersecurity needs.
How It Works
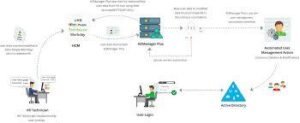
Ivanti Neurons for EASM scans your external environment continuously. It identifies assets, assesses risks, and provides remediation guidance. The platform integrates with your security stack, ensuring cohesive protection. Additionally, its dashboard offers clear, actionable insights. Teams can monitor progress and address vulnerabilities promptly.
View Ivanti Resource Document (ID: 2831)
Visit Cybersecurity Products at Kysinfotech
-
Technical Specifications
Feature Description Discovery Method Agentless, continuous internet-facing asset discovery Asset Types Detected Domains, IPs, APIs, netblocks, URLs, SSL certs Exposure Vectors Misconfiguration, patching gaps, data leaks, DNS/email insecurity Vulnerability Prioritization Risk scoring via VRS and CVSS/NVD integration Compliance GDPR, HIPAA, PCI DSS reporting support Reporting Executive summaries and detailed PDF reports Integration Options Compatible with Ivanti ITSM, UEM, and Patch Management Use Cases Third-party risk assessment, shadow IT detection, phishing defense Deployment Cloud-native SaaS model User Interface Web dashboard with workspace-based asset segmentation